Determine Which Ports Are Used in Security Hardware
Some NAC solutions can automatically fix non-compliant devices to ensure they are secure before allowing them to access the network. Place a check mark in the box titled PID.
Type netstat -ano without the quotes.

. S1config-ifswitchport port-security mac-address sticky S1config-ifswitchport port-security maximum 2 S1config-ifswitchport port-security violation shutdown. Integrity checking is used to detect and report changes made to systems. Vulnerability scanning is used to find weaknesses and misconfigurations on network systems.
If an unathorized device is connected you can decide what action the switch will take for. Simple Mail Transfer Protocol SMTP 49 TCP and UDP. Switchport port-security command is used to enables it.
Open the command prompt. Port 21 is the control protocol used with FTP. These include keyboards mice external drives microphones printers and a variety of other devices.
Receiving a UDP packet in response indicates that the port is open while an ICMP port unreachable error response signifies a closed port. Like TCP scans UDP scans send a UDP packet to various ports on a target system and evaluate the response to determine availability of the service and the host. Network access control NAC NAC is a network security control device that restricts the availability of network resources to endpoint devices that comply with your security policy.
Deep Security Relay outbound ports. Many Trojans also monitor certain ports that. The official port numbers are listed and assigned by the Internet Assigned Number Authority IANA and they divided these ports into three sub-categories.
If the user wants to provide a static entry then. As you can see this NVR comes with 8 PoE ports to connect the IP cameras and with a HDMI port to connect to it to a smart TV. -aDisplays all active TCP connections and the TCP and UDP ports on which the computer is listening.
Penetration testing is used to determine the possible consequences of successful attacks on the network. 4122 port of other Deep Security Relays. Another example is that a of DVR.
In older versions of Windows youll see this information on the Processes tab. Once you have the PID number for the port in question open Task Manager and go to the Process tab. By using port security a network administrator can associate specific MAC addresses with the interface which can prevent an attacker to connect his device.
4119HTTPS Deep Security Manager GUI and API port. Alternatively type telnet to check if port is open. Registered portsThe registered ports are those from 1024 through 49151.
If you must restrict the dynamic ports that are used with RPC you can use the Microsoft RPC configuration tool rpccfgexe. HTTPS communication between a remote management console and the SEPM. ____ software searches a node for open ports.
Type netstat -ano to list states of all ports. There are 65535 TCP and UDP ports on which a computer can communicate. Port and Protocol Threats and Mitigation Techniques.
This way you can restrict access to an interface so that only the authorized devices can use it. 80HTTP 443HTTPS Trend Micro Update ServerActive Update and Download Center ports. Displays active TCP connections however addresses and port numbers are expressed numerically and no attempt is made to determine names.
There are many security tests that can be used to assess a network. In order to configure port security we need to set it as host port. Hit Windows R to invoke Run dialog and type cmd to open Command Prompt.
The port numbers are divided into three ranges. Switch port analyzer ports. TCP port 20 and 21 are used for the file transfer protocol.
A ____ main function is to examine packets and determine where to direct them based on. Encryption is the last means of defense against data theft. Sysinternals TCPView is a Microsoft tool that makes it easy to view all the TCP connections and ports used in Windows 10 and 11.
Well-Known Ports 0-1023 Registered Ports 1024 - 49151 Dynamic Private Ports 49152 -. Terminal Access Controller Access-Control System TACACS IP protocol number 50. A blue USB port is a USB 30 and has improved connection performance.
This is also used for SCP which stands for Secure Copy a very simple copy program that uses SSH to be. As you see below this type of recorders supports BNC camera which can be CVBS analog or HD-TVIHD-CVIAHD HD-over-coax security cameras. The encrypted terminal program Secure Shell or SSH runs over TCP port 22.
SPC 2 makes Data Feed and Workflow requests to SEPM over this port. Determine What Ports are Being Used in Windows 10. This is the SEPM web services port.
Symantec Protection Center SPC 2. Well-known portsThe well-known ports are those from 0 through 1023. Displays active TCP connections and includes the.
Use IPsec to help secure the traffic between the site server and site systems. This is a standard USB Universal Serial Bus Port which allows connection communication and power supply to many types of devices. And the actual data transfer occurs over TCP port 20.
Open TCPIP ports on your servers can be an invitation to hackers especially if theyre well-known ports such as 21 FTP 80 HTTP and 25 SMTP. Electronically hardware ports can almost always be divided into two groups based on the signal transfer. A security policy should state exactly which hardware software architecture or protocols will be used to ensure security.
All login information and administrative communication takes place using this secure port. Download TCPView from the Sysinternals website extract the exe file to your desktop and double-click on it. Site server -- Distribution point.
Locate to the target port and view the corresponding PID in the final column. Port security work on host port. Port security feature does not work on three types of ports.
Use Sysinternals TCPView to check ports in use. RPC dynamic TCP ports. Encapsulating Security Payload ESP used with IPSec IP protocol number 51.
It could be done easily by switchport mode access command. Here select ViewSelect Columns. Serial ports send and receive one bit at a.
When using the AWS AMI and Azure VM versions of the manager open port 443 instead of port 4119. Sort the list of process by the PID column and find the PID associated with the port youre investigating. Parallel ports send multiple bits at the same time over several sets of wires.
If youre using Windows 8 or 10 switch to the Details tab in Task Manager. Use the tool to configure a limited range of ports for these RPC packets. The tool is very similar to CurrPorts.
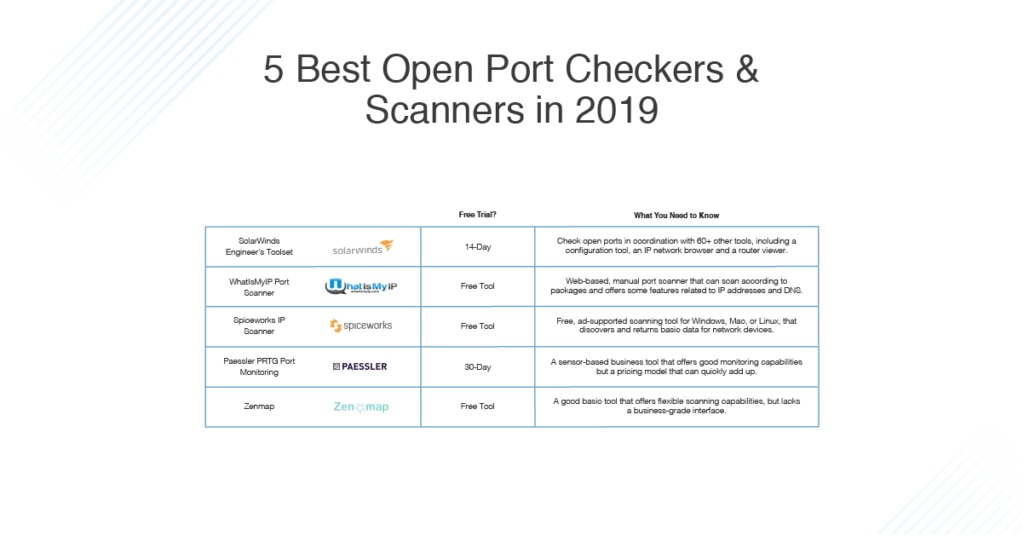
5 Best Open Port Scanners And Checkers Dnsstuff
/cdn.vox-cdn.com/uploads/chorus_image/image/63092476/akrales_190220_3226_0003.0.jpg)
The Best Hardware Security Keys For Two Factor Authentication The Verge

Is Firewall Blocking Your Quickbooks Programs Then You Need To Update Your Firewall To Latest Version Or Manually Config Quickbooks Internet Security Security

Network Security Malwareanalysis Cyber Security Education Cyber Security Awareness Cyber Security

Comments
Post a Comment